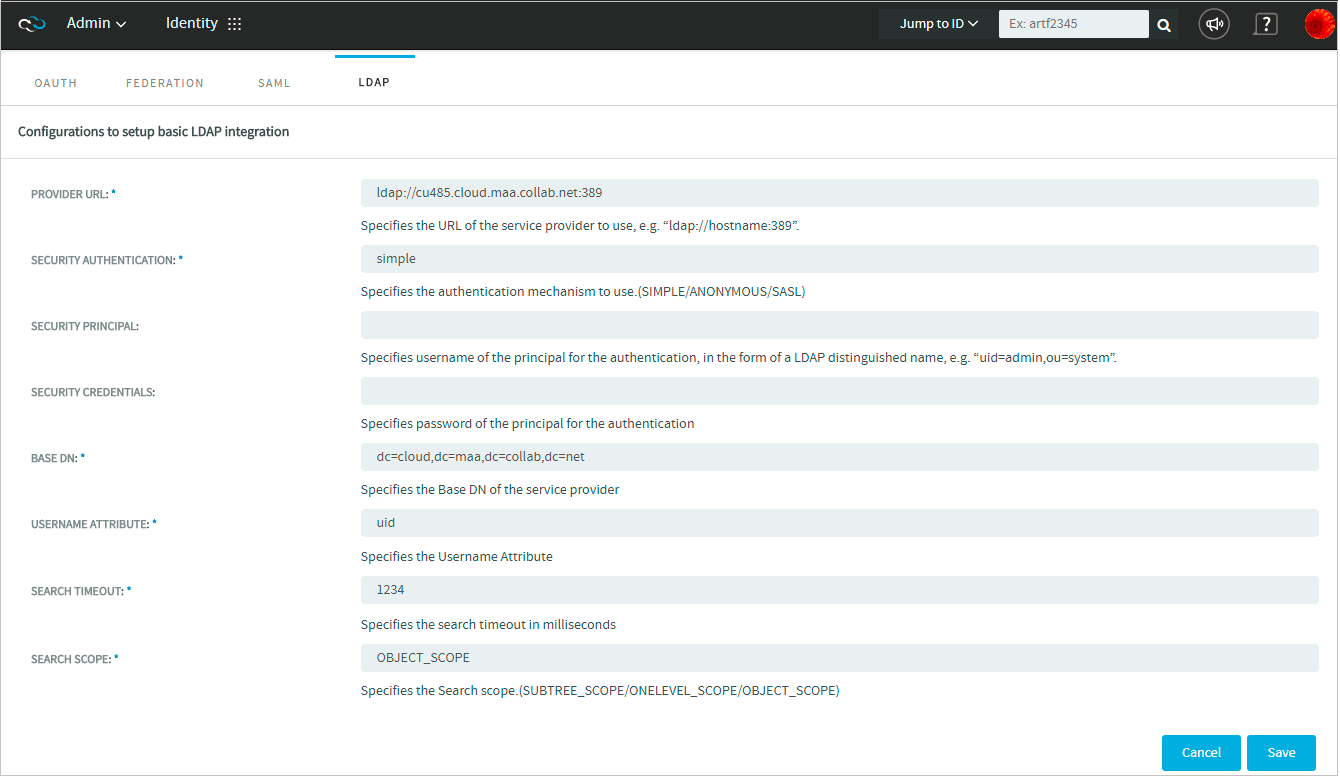
In this section, you can see how to make LDAP as an IdP in TeamForge and how to configure TeamForge for enabling LDAP driven authentication.
Important: Contact CollabNet Support before you set up the TeamForge LDAP on
your site.
Preparing TeamForge for LDAP integration
- USE_EXTERNAL_USER_AUTHENTICATION - Set this token to True.
- ALLOW DATABASE AUTHENTICATION IF LDAP IS
ENABLED - Select this check box to have LDAP
credentials stored in TeamForge and have users authenticated via TeamForge
every time a user logs in. This helps improve performance by optimizing the
number of authentication calls between TeamForge and LDAP server. To select
this check box, navigate to and then to page. This parameter is shown under the section
External Authentication.Important: Enabling this parameter is mandatory for sites with internally managed CVS servers.Note: TeamForge administrators can restrict the users from logging into TeamForge using database authentication after a specific duration by setting the timeout period after which the users would be forced to log on to TeamForge only via LDAP authentication. The parameter "Forge Re-authentication with LDAP Server" parameter denotes the timeout period after which the user authentication into TeamForge is done via LDAP authentication. For more information on this parameter, see FORCE RE-AUTHENTICATION WITH LDAP SERVER.
- APPROVE_NEW_USER_ACCOUNTS - Set this token to False .
- REQUIRE_PASSWORD_SECURITY - Set this token to False.
- LINUX_USERNAME_MODE_ENABLED - Set this token to True.
- MINIMUM_PASSWORD_LENGTH - Set the value of this token to '0'.
- PASSWORD_REQUIRES_MIXED_CASE - Set this token to False.
- PASSWORD_REQUIRES_NON_ALPHANUM - Set this token to False.
- PASSWORD_REQUIRES_NUMBER - Set this token to False.
- REQUIRE_USER_PASSWORD_CHANGE - Set to token to False.
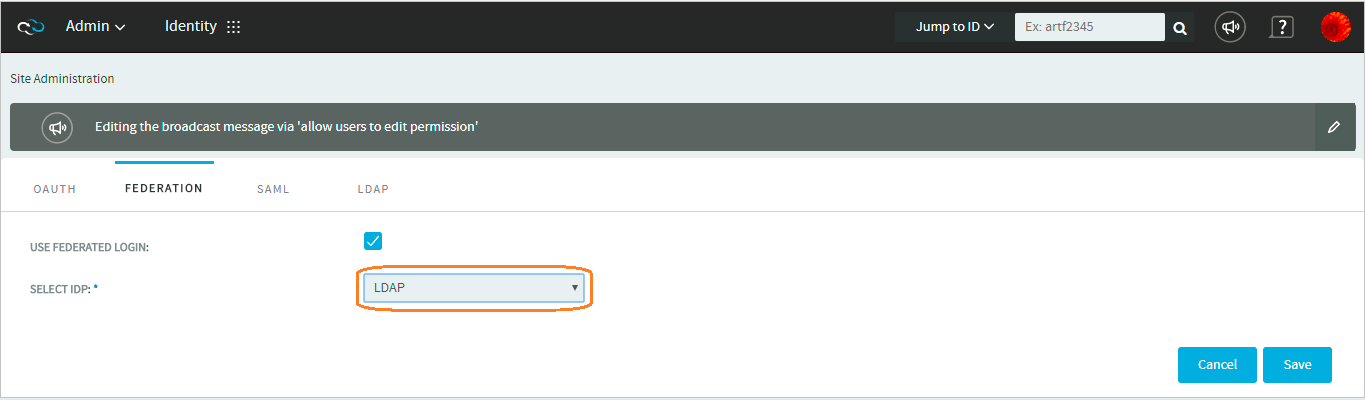
Enabling LDAP as an IdP
You need to enable LDAP as an IdP to facilitate LDAP based authentication for TeamForge users.